This site is obsolete. Please visit https://tigress.wtf.
Tigress is a diversifying virtualizer/obfuscator for the C language that supports many novel defenses against both static and dynamic reverse engineering and de-virtualization attacks.
In particular, Tigress protects against static de-virtualization by generating virtual instruction sets of arbitrary complexity and diversity, by producing interpreters with multiple types of instruction dispatch, and by inserting code for anti alias analysis. Tigress protects against dynamic de-virtualization by merging the real code with bogus functions, by inserting implicit flow, and by creating slowly-executing reentrant interpreters. Tigress implements its own version of code packing through the use of runtime code generation. Finally, Tigress' dynamic transformation provides a generalized form of continuous runtime code modification.- A new unstable version is now available. There are some major updates:
- The RandomFuns transformation has been updated. It can now generate multiple functions, global data, heap-based data structures, and switch statements. The random control flow generation is also vastly improved.
- A new --Skip=true/false option has been added, that allows you to turn on and off particular transformations. This is useful when you want to apply multiple transformations, and see what happens when particular transformation subsets are used.
- A new implicit flow training kind has been added, called resend, in addition to the previous one now called gap. This provides statistical correctness guarantees.
- A new EncodeExternal transformation was added. It makes a simple attempt at hiding calls to external functions, such as system calls.
- The --Environment=... option is now mandatory.
- --Transform=... --Verbosity=1 will now print out some statstics on how successful a transformation was, for example how many times a function could be split, the number of gotos that the EncodeBranches transformation could replace, etc.
- Christian gave an invited talk at CODASPY-2018.
- Our paper Probabilistic Obfuscation through Covert Channels, by Jon Stephens, Babak Yadegari, Christian Collberg, Saumya Debray, and Carlos Scheidegger, was presented by Jon at 3rd IEEE European Symposium on Security and Privacy! The paper covers the probabilistic implicit flow transformation of Tigress.
- Jonathan Salwan solved
challenges 0000, 0001, 0002, 0003, and 0004! The results were published in DIMVA 2018, in the
paper Symbolic Deobfuscation: From Virtualized Code Back to the Original,
by Jonathan Salwan, Sébastien Bardin, and Marie-Laure Potet.
- Frederic Perriot solved challenge 0005!
- Tigress v 2.2 is now available for download! New features include support for branch functions on ARM v7 (Raspberry Pi).
- I will be giving an invited talk at ACSAC'17 in Orlando, December 7, 2017.
- Jonathan Salwan solved some of our challenges!
- Sebastian Millius solved challenge 0000!
- The slides from my Eurocrypt 2016 invited talk are here. The talk itself is here.
- Our paper Code Obfuscation Against Symbolic Execution Attacks (Sebastian Banescu, Christian Collberg, Vijay Ganesh, Zack Newsham, Alexander Pretschner) won the Outstanding Paper Award at ACSAC'16!
- Our paper Predicting the Resilience of Obfuscated Code Against Symbolic Execution Attacks via Machine Learning (Sebastian Banescu, Christian Collberg, Alexander Pretschner) was presented at USENIX Security'17.
Design
Tigress is a source-to-source transformer built in OCaml on top of CIL and MyJit:
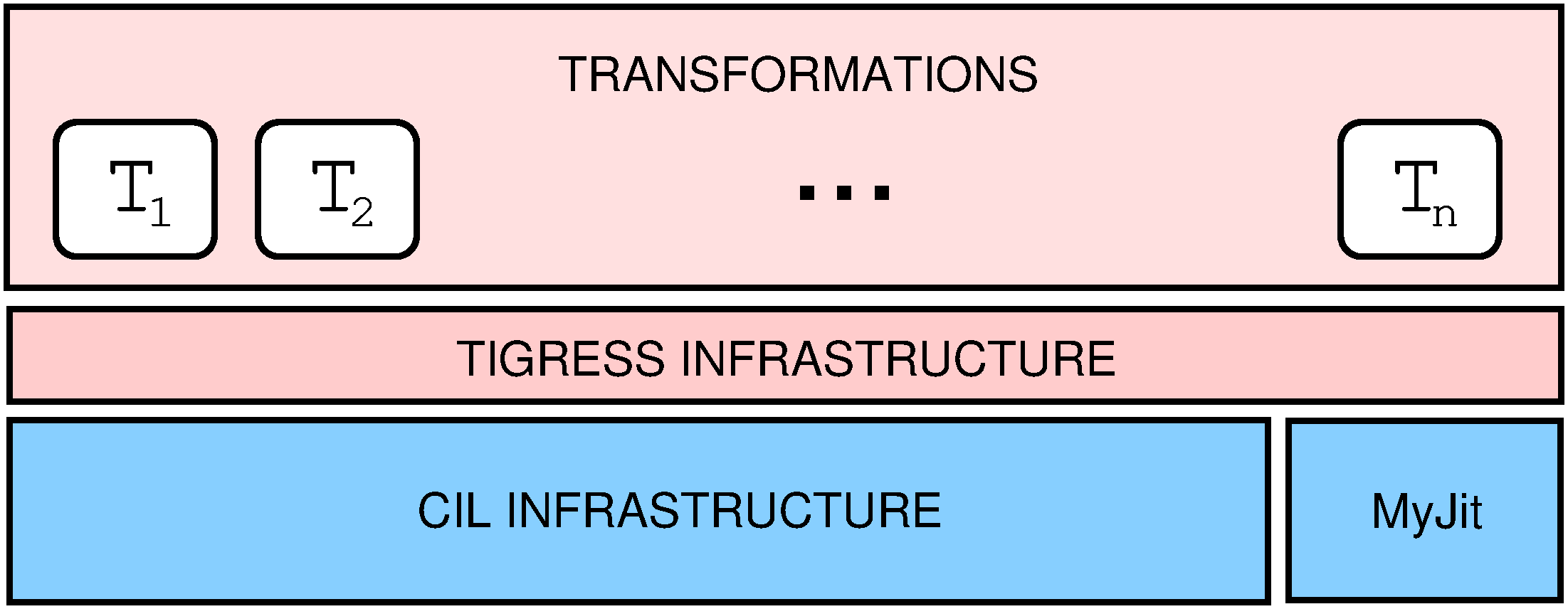
Tigress supports all of the C99 language, including gcc extensions. The source-to-source design means that the transformed code can be easily examined, which is useful in a pedagogical setting. Also, Tigress' output, once compiled and stripped of symbols, is a good target for reverse engineering and de-virtualization exercises. Tigress' design is similar to that of commercial tools, such as Cloakware/IRDETO's C/C++ Transcoder.
The user interacts with Tigress by giving an input C file, a seed, and a sequence of transformations:
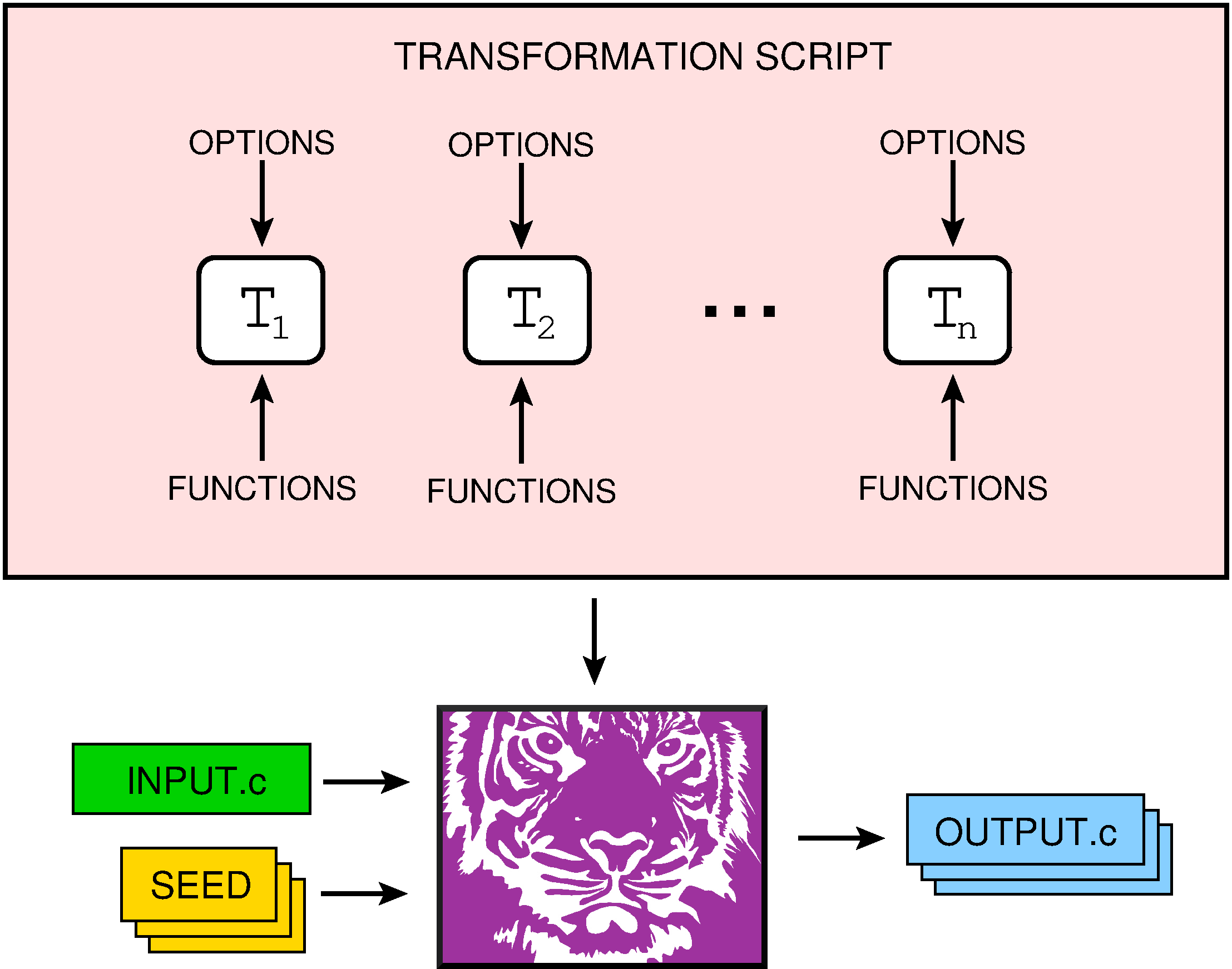
Transformations
Tigress supports three major transformations:
- Virtualization, i.e. transforming a function into an interpreter whose bytecode language is specialized for this function, and
- Jitting, i.e. transforming a function into one that generates its machine code at runtime.
- JitDynamic, i.e. transforming a function into one that continuously modifies its machine code at runtime.
In addition, Tigress has a collection of supporting transformations that can help with resilience to attack, diversity, and stealth:
- Control flow flattening,
- function Splitting, Merging, and Argument randomization,
- Control flow splitting with opaque predicates,
- encoding of Literals, Data, and Arithmetic.
Tigress also supports three transformations designed to thwart particular static and dynamic analyses:
Diversity
Tigress is designed such that, from a single source program, it is possible to generate large numbers of highly diversified variants. This diversity is both static and dynamic, i.e. two variants will differ both in their machine code and in the resulting instruction traces. In essence, every decision Tigress makes is dependent on a randomization seed, controllable by the user. There are two major sources of diversity:
- Tigress goes to great lengths to provide as many variants of each transformation as possible. For example, our virtualization transformation supports eight kinds of dispatch, can generate arbitrarily complex virtual instruction sets, and can generate instructions which arbitrarily mix stack and register operands.
- Tigress' transformations can be combined in arbitrary ways, such as virtualizing a virtualized function, jit two merged functions, virtualize a jitted function, etc.
Applications
Research: Tigress was originally designed as the backend of a system for remote attestation. The idea was to force rapid updates to the code running on an untrusted remote site in order to increase the workload of the attacker who has to crack, and re-crack, the code as it is constantly updated.
Other applications of Tigress include:
- We are currently using Tigress to measure the stealth of obfuscated code.
- One group is using Tigress to develop A Framework for Measuring Software Obfuscation Resilience Against Automated Attacks.
- Another group is using Tigress to test code stylometric algorithms.
- Federico Scrinzi is using Tigress to generate obfuscated code to analyze in his University of Twente Master's Thesis Behavioral Analysis of Obfuscated Code.
- Mark Janssen's Master's Thesis Combining learning with fuzzing for software deobfuscation uses Tigress to generate obfuscated code to analyze.
- Johannes Kinder is using Tigress to study static analysis of virtualized code, Towards Static Analysis of Virtualization-Obfuscated Binaries, WCRE'12.
- In their paper Trading Off a Vulnerability: Does Software Obfuscation Increase the Risk of ROP published in the Journal of Cyber Security and Mobility Harshvardhan P. Joshi, Aravindhan Dhanasekaran and Rudra Dutta use Tigress for evaluation purposes.
- Pierre Graux uses Tigress to study de-virtualization in his paper Désobscurcissement de programmes virtualisés.
- Tsong Yueh Chen, Fei-Ching Kuo, Wenjuan Ma, Willy Susilo, Dave Towey, Jeffrey Voas, and Zhi Quan Zhou use metamorphic testing to find bugs in Tigress! See Metamorphic Testing for Cybersecurity.
- Robin David, Sébastien Bardin, Jean-Yves Marion use Tigress in their paper Targeting Infeasibility Questions on Obfuscated Codes to study the effectiveness of Dynamic Symbolic Execution.
- Sebastian Banescu, Christian Collberg, Vijay Ganesh, Zack Newsham, and Alexander Pretschner describe an extension to Tigress in their paper Code Obfuscation Against Symbolic Execution Attacks.
- William D. Holder, Master's thesis, EVALUATING OPTIMAL PHASE ORDERING IN OBFUSCATION EXECUTIVES.
- Predicting the Resilience of Obfuscated Code Against Symbolic Execution Attacks via Machine Learning, Sebastian Banescu, Christian Collberg, Alexander Pretschner, USENIX Security'2017.
- Thomas Rinsma, in his Masters's Thesis Seeing through obfuscation: interactive detection and removal of opaque predicates, attacks Tigress' opaque predicates.
- Anatoli Kalysch, Oskar Milisterfer, Mykolai Protsenko, Tilo Müller, Tackling Androids Native Library Malware with Robust, Efficient and Accurate Similarity Measures, ARES 2018 Proceedings of the 13th International Conference on Availability, Reliability and Security.
- A. Salem, GoldRusher: A miner for rapid identification of hidden code, 2018 IEEE 25th International Conference on Software Analysis, Evolution and Reengineering (SANER).
Benchmarking: We are planning to use Tigress to generate collections of software protection benchmark programs. These will provide the community with randomly generated attack targets to form a basis for uniform and generally accepted evaluation procedures for software protection algorithms. In particular, we are hoping future de-virtualization research projects will use Tigress-generated interpreters as one of their attack targets.
Challenges: To stimulate reverse engineering research, we are publishing sets of challenge problems generated by Tigress. Prizes will be awarded to those who are first to crack.
Education. In our classes we use Tigress to generate reverse engineering exercises and take-home exams for the students. We use Tigress' RandomFuns transformation to generate a unique random program for every student in the class and protect it using some appropriate combination of transformations. The difficulty of the exercises can be easily varied by picking different sequences of transformations, and, since diversity guarantees that every program instance is unique, cheating is made more difficult.